What is MEV in Crypto: Its Protection and Automation with Bot


Maximal extractable value, popularly known as MEV, refers to the maximum value miners or network validators can extract by rearranging and reordering transactions waiting to be added to the blockchain.
Picture yourself as a miner or validator in a decentralized blockchain ecosystem. Your goal is to process transactions within the block. But your other goal is, of course, to maximize your income by doing this little service for the network. Miner Extractable Value (MEV) is the additional profit miners or validators can earn by strategically reordering, including, or censoring transactions within the blocks in addition to the standard reward for mined blocks.
This practice significantly affects transaction fees, user experience, and fairness across blockchain networks. Originally, MEV was specific to miners. However, as Proof-of-Stake (PoS) and other consensus mechanisms emerged, it became clear that other entities, such as validators or sequencers, could exploit these opportunities as well. This evolution has led to a broader term: Maximum Extractable Value (MEV, again). Any block producer can extract the “maximum” value by manipulating transaction ordering.
MEV can be viewed as a double-edged sword. While some forms of MEV extraction improve market efficiency (e.g., arbitrage), others harm users and reduce trust in decentralized applications. For developers, understanding the history and nuances of MEV’s evolution—from a PoW-specific term to a universal concept—helps design fair and efficient applications.
[.c-wr-center][.button-black]Start Now[.button-black][.c-wr-center]
Especially on high-volume chains supporting DeFi and complex transactions, MEV holds considerable value as opportunities for profit increase. In some cases, it can drive up gas fees and create worse trading conditions for regular users.
MEV doesn’t just affect users directly involved in the extracted transactions. By driving up gas fees through competitive bidding wars, MEV can indirectly raise transaction costs across the network.
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: gRPC vs. RPC: Comparing Protocol Buffers, JSON, Avro, and Thrift[.c-text-center][.c-box][.c-box-wrapper]
During peak times, high transaction fees can discourage users from interacting with DeFi protocols altogether. This is why MEV awareness is essential not only to optimize protocol performance but also to protect users and contribute to the integrity of the decentralized ecosystem.
Before we jump into the chapter, there is one important note: Not every MEV strategy is unethical or has only negative consequences for the users. Some can even be helpful and standard occurrences on any market, such as arbitragining. On the other hand, some methods akin to frontrunning are often illegal in the traditional market. However, at the time of the writing, there was no regulation for the cryptocurrency market. Still, traders seek ways to protect from MEV strategies like frontrunning.
From a developer's or manager's point of view, MEV presents a problem that might discourage people from using the platform, thereby lowering potential profit from fees.
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: Understanding Mempool in Blockchain[.c-text-center][.c-box][.c-box-wrapper]
Arbitrage in MEV involves bots taking advantage of price discrepancies for the same asset across different decentralized exchanges (or DEX). Here’s how it typically works:
Frontrunning occurs when a malicious actor detects a pending transaction in the blockchain mempool, such as a sizeable token purchase. Then, it submits its own transaction to be mined immediately before it:
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: Fact or Myth: Gateways Always Outperform Direct RPC Endpoints[.c-text-center][.c-box][.c-box-wrapper]
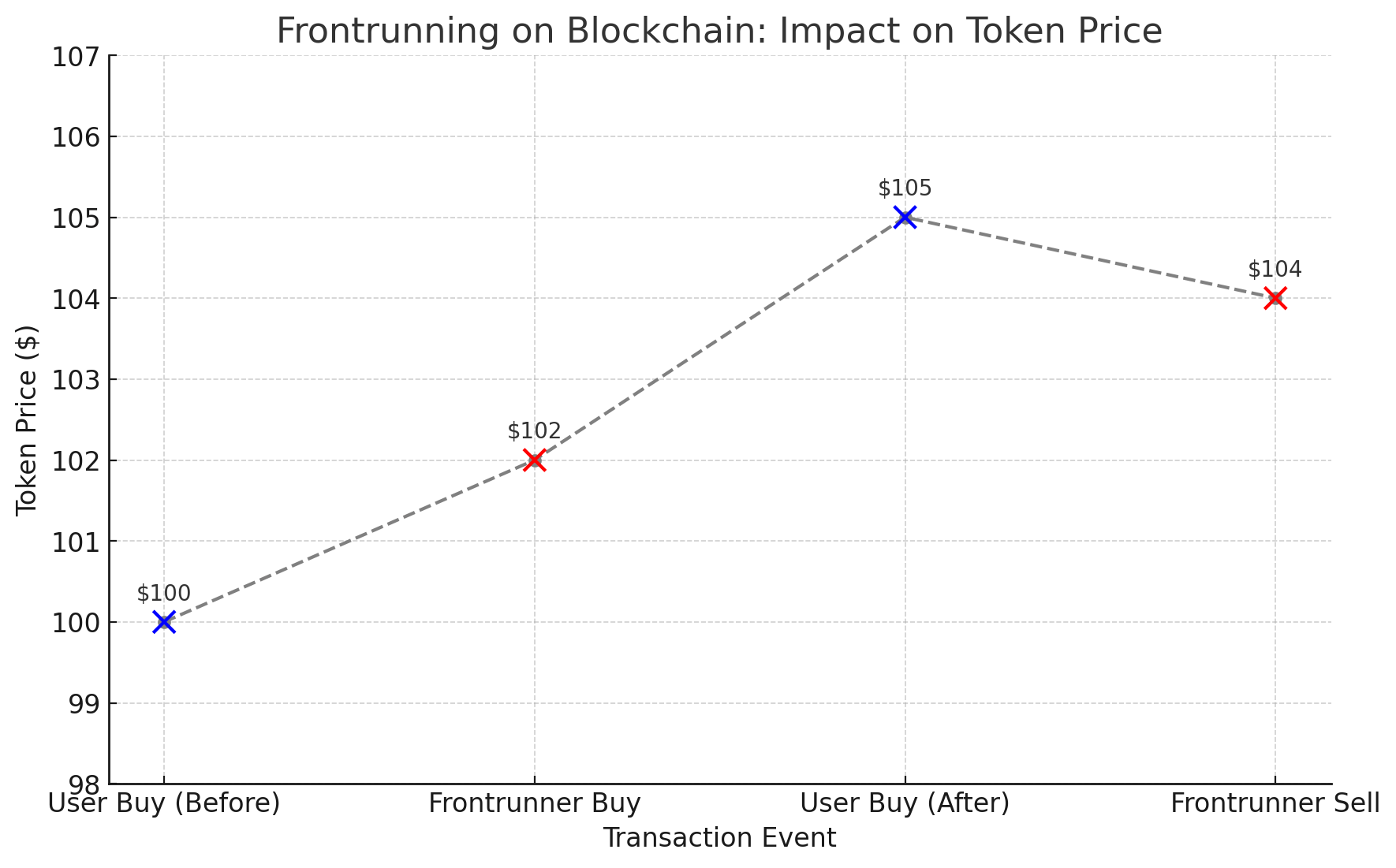
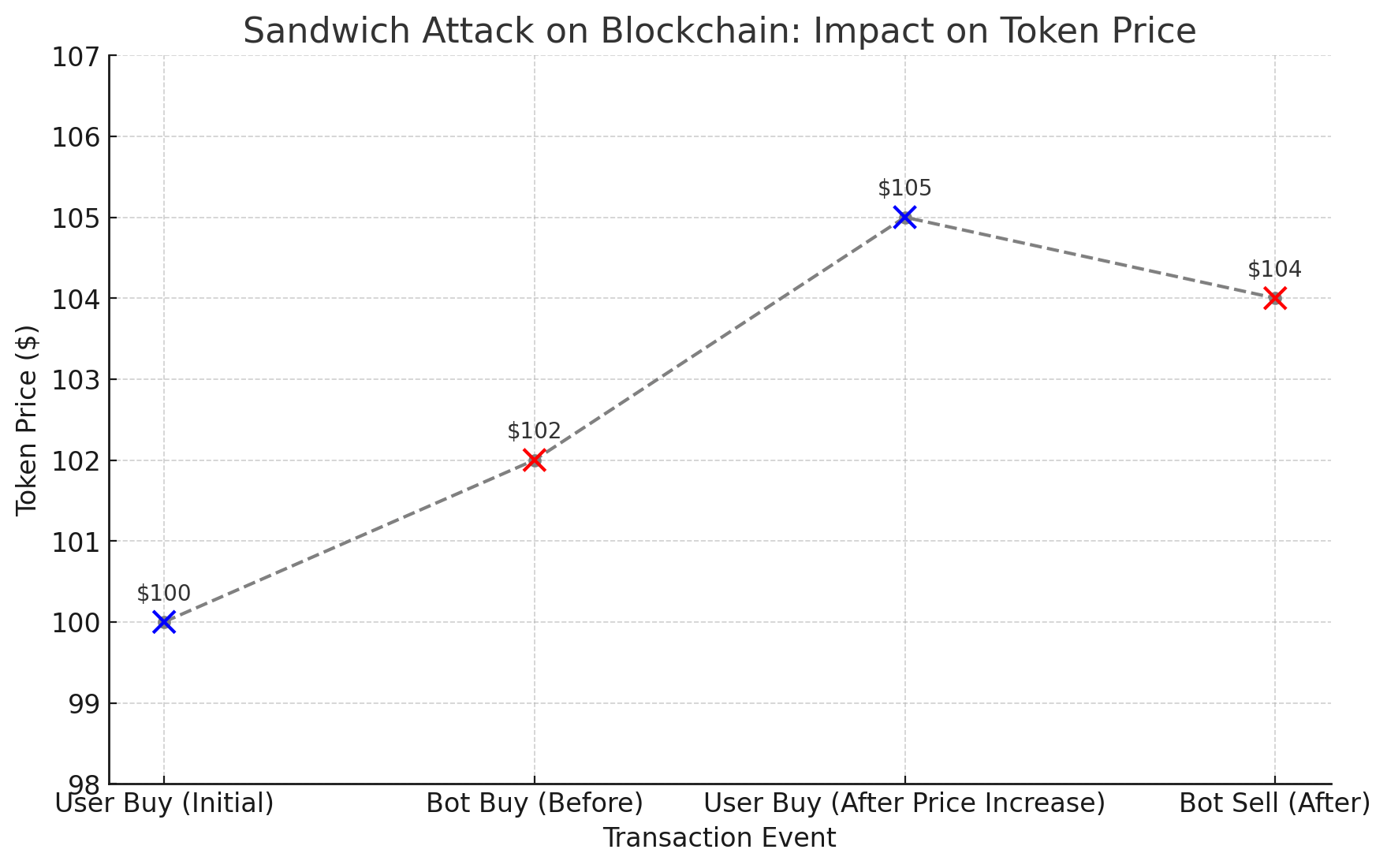
Sandwich attacks are a more complex form of frontrunning, exploiting the fact that trades impact token prices:
This one is a bit different because it is a part of how smart contract exchanges operate and does not hurt users directly. Many DeFi lending platforms use collateral-based lending, where users risk liquidation (the platform forcefully sells their assets to pay for the debt) if their collateral value falls below a threshold:
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: How to Become a Blockchain Developer: Ultimate Guide[.c-text-center][.c-box][.c-box-wrapper]
Here are some real-world cases where MEV has affected users to illustrate the concept’s scope and impact:
In 2021, a well-known sandwich attack on Uniswap caused significant losses for users. A bot detected a pending large buy order, submitted a buy order right before it, and a sell order immediately after, profiting from the price increase. This tactic left the user with a substantially worse price. If this was classified as theft of assets, it would be the second largest “hack” of 2021, extracting $254 million dollars from everyday users.
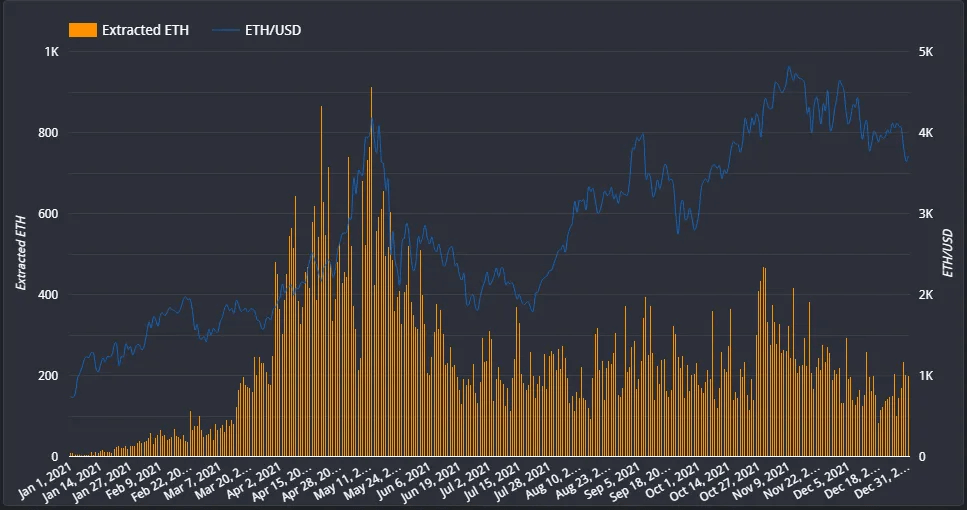
In another example, liquidation bots on Compound took advantage of market volatility. During a sharp price drop, bots raced to liquidate under-collateralized positions. The competition drove gas fees sky-high, hurting network users who were not directly involved in the liquidations but also preserving the solvency of the smart contract.
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: Decoding Blocks: The Pillars of Crypto Innovation[.c-text-center][.c-box][.c-box-wrapper]
Several mitigation strategies have been developed by the blockchain industry due to MEV’s potential for abuse:
Some DeFi protocols are adopting designs to reduce MEV vulnerabilities. For example, Curve Finance uses bonding curves to minimize price impact on trades. A smaller price impact means sandwich attacks are less profitable, and the bot operation might not be worth it any more. Other protocols, like MakerDAO, set fixed parameters on liquidations to prevent costly gas bidding wars. Aave’s flash loans facilitate liquidations without requiring high upfront capital, reducing MEV bots' advantages.
Additionally, batch auctions and sealed-bid mechanisms are being explored to counteract MEV. Batching groups trades to make them execute in a single time point. Therefore, the MEV bot cannot manipulate order flow for profit.
Flashbots is an Ethereum-based solution that addresses frontrunning and sandwich attacks by creating a private transaction pool.
Users can submit transactions privately to Flashbots, which delivers them directly to miners rather than broadcasting them to the public mempool. This prevents other bots from detecting and frontrunning these transactions.
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: Smart Contracts: The Backbone of Decentralized Applications[.c-text-center][.c-box][.c-box-wrapper]
However, Flashbots isn’t without criticism; some argue it introduces centralization risks by routing transactions through specific miners.
Some DeFi protocols and DEX aggregators support transaction batching. Users are enabled to bundle multiple actions into a single transaction, effectively having them executed at a single point in time.
By bundling trades, users can reduce MEV exposure since it’s harder for bots to isolate individual trades within a batch.
It’s particularly helpful for users conducting multiple DeFi operations in a single transaction.
Specific blockchains are experimenting with fair sequencing to mitigate MEV. It works by introducing randomized transaction ordering:
This approach, pioneered in networks like Optimism, aims to create fair ordering by using decentralized sequencers. Because of the randomness, a layer of security for users is added, protecting them from frontrunning and sandwich attacks.
Sequencer randomness and unpredictability add a layer of security for users against frontrunning and sandwich attacks.
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: Tracking Internal Transactions on Ethereum[.c-text-center][.c-box][.c-box-wrapper]
This is not a one-size-fits-all solution, but including it along with its benefits and limitations gives a more comprehensive view of the MEV mitigation landscape. Developers can choose a mix of suitable solutions based on their applications and user base.
MEV strategies and protections vary from one blockchain to another due to differences in consensus algorithms, transaction fees, and ecosystem maturity. Here’s how MEV manifests in some popular networks:
[.c-box-wrapper][.c-box][.c-text-center]You might be interested in: What Are Blockchain Validiums, and How They Work[.c-text-center][.c-box][.c-box-wrapper]
Some of the MEV methods are illegal in traditional markets. Therefore, it is relevant to stop by and discuss the aspects of regulation.
Due to its potential to undermine fairness in decentralized finance, the regulation of MEV strategies is being discussed increasingly. There are ongoing debates around self-regulation within the industry, especially as the importance of maintaining transparency and fairness grows. Protocol safety is one of the main concerns of blockchain users, so the self-regulation and development of solutions is a viable option.
A combination of efforts on both the user's and developer's sides will mitigate the MEV attacks in the future.
Developers can incorporate design strategies to reduce users' vulnerability to MEV, making applications more resilient:
Finally, a few simple strategies for users can reduce MEV-related risks:
[.c-wr-center][.button-black]Get Started[.button-black][.c-wr-center]
Build blockchain apps faster with a unified framework for 60+ blockchain protocols.