What Are Decentralized Identifiers?


Decentralized identifiers (DID; plural DIDs) allow users to control their digital identities. Unlike traditional digital identifiers like email or a username, they do not rely on centralized authorities for management and verification. One such centralized authority could be Google or Microsoft. The main difference is that in the case of DIDs, only the user has control over the identity. Decentralized identifiers are globally unique and can be resolved to DID Documents, which describe how to interact with them.We will explore the concept of decentralized identifiers, their functionality, applications, and benefits. Moreover, we will discuss the link between DIDs, verifiable credentials, and blockchain technology.
Key Characteristics of Decentralized Identifiers
A DID Document is a JSON-LD file that contains essential information about a decentralized identifier like public keys, authentication methods, and service endpoints. It serves as the basis for verifying the identity and authenticity of the DID owner.
A DID Document is a JSON-LD file that contains essential information about a decentralized identifier like public keys, authentication methods, and service endpoints. It serves as the basis for verifying the identity and authenticity of the DID owner.
Example of a DID Document or a Decentralized Identifier:
[.c-wr-center][.button-black]Sign Up[.button-black][.c-wr-center]
DID methods define how decentralized identifiers are created, resolved, updated, and deactivated on specific blockchain networks. Each method corresponds to a unique scheme and underlying technology. For example, “did:ethr” for Ethereum-based identifiers or “did:sov” for Sovrin-based ones.
Verifiable credentials (VC; plural: VCs) are digital statements that assert certain attributes about a DID subject. This can include, among other things, education, certification, or employment history. VCs are cryptographically signed by an issuer and can be independently verified by any party. VCs enhance the trust and utility of decentralized identifiers by providing attestations about the identity, qualifications, or attributes of the owner.
Example of a Verifiable Credential:
The World Wide Web Consortium (W3C) has developed a standard that defines the structure, operation, and interoperability of any decentralized identifier. According to the W3C, a DID is a globally unique identifier that can be resolved to a DID Document. This document contains the cryptographic material and other metadata required to authenticate the owner and facilitate trusted interactions.
ERC 1056, also known as the “Lightweight Identity” standard, is an Ethereum Improvement Proposal that defines an interface for managing decentralized identifiers on the Ethereum blockchain. It aims to provide a simple and efficient method for creating, updating, and deactivating DIDs using Ethereum smart contracts.
ERC 1056 proposes the use of a smart contract called the “EthereumDIDRegistry.”
This registry contract allows users to:
The main goal of ERC 1056 is to offer a lightweight and flexible identity management solution that leverages the security and transparency of the Ethereum blockchain without the complexity and overhead of more extensive identity frameworks.
The EthereumDIDRegistry contract is the core component of the ERC 1056 standard. It provides functions to manage the lifecycle of decentralized identifiers; creation, updates, and revocation. Using access control mechanisms, the contract safeguards that only authorized entities can perform these operations.
Key Functions of the EthereumDIDRegistry Contract:
[.c-box-wrapper][.c-box]You might be interested in: What Is a Nonce in Blockchain: Definition and Purpose[.c-box][.c-box-wrapper]
Blockchain technology provides a solid infrastructure for managing decentralized identifiers. By leveraging the decentralized and immutable nature of blockchains, identifiers can be securely created, managed, and verified without relying on any authority.
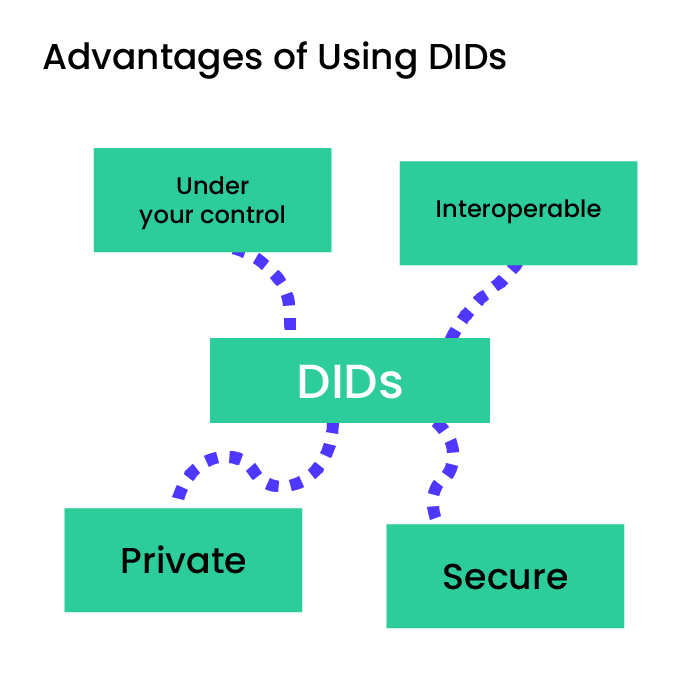
Decentralized systems eliminate central points of control, reducing the risk of data breaches and unauthorized access. Each identifier is cryptographically secure, and the associated DID Document makes it so that only the legitimate owner can control and update their identity information.
Using decentralized identifiers, organizations can put into action privacy-preserving identity solutions. Individuals can selectively disclose their information, and verifiable credentials can prove attributes without revealing unnecessary details.
DIDs are designed to be interoperable across different systems and platforms. Organizations can adopt a unified identity framework that works seamlessly with various applications and services, reducing integration complexities.
Users can manage their identities independently and securely without relying on external authorities, which fosters good relationships between organizations and individuals.
[.c-wr-center][.button-black]Get Started[.button-black][.c-wr-center]
Build blockchain apps faster with a unified framework for 60+ blockchain protocols.