What Is Zcash? Understanding the Privacy Blockchain


%20(16).jpg)
Privacy is often talked about in Web3, but very few blockchains are actually designed around it.
For many builders, transparency is useful until it becomes a liability. Payments, treasuries, identities, payroll, and even DeFi strategies can leak far more information than intended when everything is public by default.
Zcash exists precisely to address this problem. It is a blockchain built with privacy as a core protocol feature, not an afterthought. In this piece, we look at how Zcash works, why it matters for developers, and how teams can practically build privacy-aware applications on top of it using modern infrastructure.
Zcash is a blockchain protocol derived from Bitcoin’s original codebase, but extended with advanced cryptography that allows transactions to be verified without revealing sensitive details. The protocol defines the network rules, while ZEC is the native asset used for value transfer.
The original goal behind Zcash was simple but ambitious, make digital money that preserves financial privacy without compromising security or decentralization. The project emerged from academic research in zero-knowledge proofs and has remained closely aligned with that research-driven mindset ever since.
Most blockchains are transparent by design. Anyone can inspect balances, transaction histories, and interactions between addresses. While this openness enables auditability, it also introduces real issues for both users and developers.
Transparent ledgers make it easy to track spending habits, infer business relationships, front-run strategies, or deanonymize users through data correlation. For many applications, this is not a feature but a risk.
Zcash takes a different approach by allowing privacy at the protocol level, without relying on mixers or external tooling.
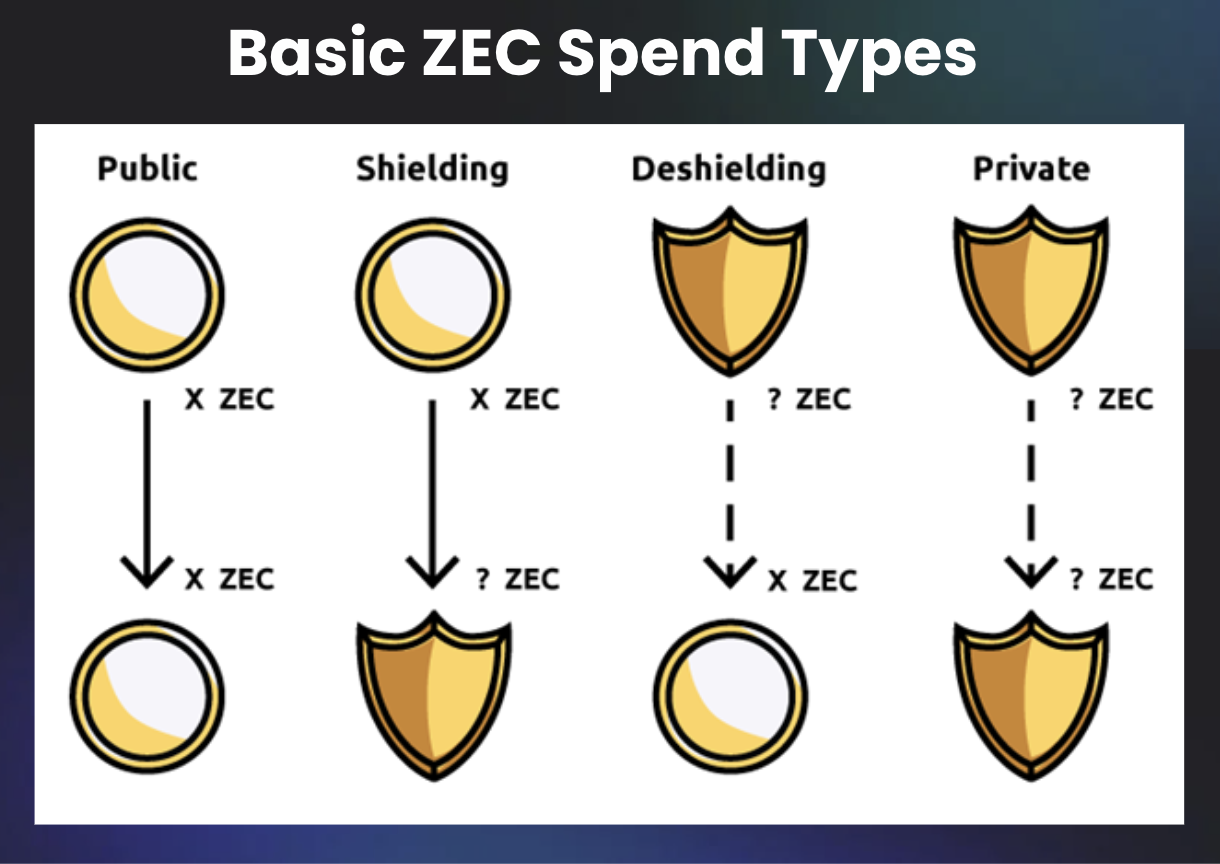
Zcash supports two types of transactions, transparent and shielded.
Transparent transactions behave similarly to Bitcoin. Addresses and amounts are publicly visible on-chain.
Shielded transactions use zk-SNARKs, a form of zero-knowledge proof, to encrypt transaction data. The network can still verify that the transaction is valid, but observers cannot see the sender, recipient, amount, or memo.
For developers, this dual model is important. It allows flexibility. Applications can choose when transparency is acceptable and when privacy is required, rather than forcing a single approach.
Because privacy is native to the protocol, Zcash is particularly relevant for use cases where confidentiality is essential, not optional.
Common examples include private payments and remittances, treasury management, payroll systems, identity and credential flows, and compliance-sensitive financial applications. In these contexts, leaking on-chain data can create legal, operational, or competitive problems.
Zcash gives builders primitives that make privacy the default outcome instead of something that needs to be engineered around.
Running Zcash nodes is not trivial. Modern Zcash implementations, including Zebrad, require ongoing maintenance, upgrades, monitoring, and redundancy to be production-ready. For many teams, this quickly becomes a distraction from actual product development.
This is where managed infrastructure becomes useful, not as a selling point, but as a practical necessity.
Tatum provides hosted access to Zcash through a unified RPC Gateway. The goal is straightforward, give developers a reliable way to interact with the Zcash network without managing nodes themselves.
What matters here is not branding, but surface area and reliability. The Zcash integration exposes both Mainnet and Testnet environments, supports standard JSON-RPC as well as REST interfaces, and includes Zebrad JSON-RPC for teams that want to work with modern Zcash nodes.
Through the gateway, developers can connect to:
| Network | Available Interfaces |
|---|---|
| Zcash Mainnet |
JSON-RPC endpoint REST API Zebrad JSON-RPC |
| Zcash Testnet |
JSON-RPC endpoint REST API Zebrad JSON-RPC |
The supported methods cover block and chain data, mempool inspection, raw transaction handling, fee estimation, and transaction submission. This allows to build wallets, backends, analytics pipelines, and privacy-aware services on top of Zcash.
For developers who prefer to explore APIs interactively, Zcash RPC methods are available through a pre-configured Postman collection. This makes it easy to inspect responses, validate assumptions, and experiment with calls before integrating them into an application.
It is particularly useful when working with a UTXO-based chain like Zcash, where understanding transaction structure and node responses early can save time later.
Zcash is designed for apps where privacy is not optional. If the privacy of your users matters, you know what to do.
Get your free API key ASAP!Zcash is not trying to be everything. It is not an EVM clone, and it does not optimize for maximal composability. Instead, it focuses on one problem and solves it deeply, privacy.
If you are building applications where confidentiality is a requirement rather than a bonus, Zcash remains one of the most credible options in the ecosystem. With modern infrastructure abstractions, the barrier to entry is far lower than it used to be.
Build blockchain apps faster with a unified framework for 60+ blockchain protocols.